The Everyday French Chef is a cooking blog, but as it happens this particular food blogger is also a journalist with a background in investigative reporting. What follows is my report on how cybercriminals penetrated this web site with links offering ‘payday loans’ at high interest rates – a scheme that could also aim to lure the unwary into revealing personal information to internet fraudsters involved in the multimillion dollar business of identity theft. I followed them along an international trail that led from Czech Republic to Russia, Canada, Germany and the United States. The technique they used is called ‘cloak hacking.’
◊
 First, let me introduce myself. I’m Meg Bortin, an American journalist, writer and food blogger based in Paris. Last autumn I launched The Everyday French Chef, where I post recipes twice a week. The site is totally nonprofit. My sole aim has been to attract a sufficient following to be able to publish a cookbook. While the site has proved successful, it hasn’t gone viral in the way I hoped it might. With fewer than 300 followers, I never imagined that cybercriminals would taken an interest in me.
First, let me introduce myself. I’m Meg Bortin, an American journalist, writer and food blogger based in Paris. Last autumn I launched The Everyday French Chef, where I post recipes twice a week. The site is totally nonprofit. My sole aim has been to attract a sufficient following to be able to publish a cookbook. While the site has proved successful, it hasn’t gone viral in the way I hoped it might. With fewer than 300 followers, I never imagined that cybercriminals would taken an interest in me.
I was alerted to the fact that there was a problem just over a week ago, when my brother in California forwarded the email update he had received from my site that morning. To my surprise, above my link to a recipe for fresh sorrel soup was another link, not inserted by me, saying ‘INSTANT payday loans online.’ I clicked on the link and found myself on a site called blatpaydayloans.com soliciting readers to apply for quick cash advances. I thanked my brother and got in touch with a French web designer who helps me with technical aspects of the site.
At first we thought the problem was emanating from Feedburner, a Google service that sends out email updates each time I put up a new blog post. My French consultant suggested that I change my Feedburner password, which I did, before putting up a new post. Unfortunately, the email update for this post, too, was penetrated by an intruder. Inserted above the link to my recipe for rhubarb-strawberry soup, it said ‘additional info.’ I clicked on the link and found myself on payday2loans3.com, another cash-advance site.
A payday loan, I was to learn, is a short-term loan meant to be repaid by the borrower’s next payday. Interest rates are astronomical. For example, a borrower might be charged $15 in interest on a 2-week loan of $100. That works out to an interest rate of 390 percent a year. But at a time when many people are suffering from the economic downturn, it’s not hard to imagine that, as the bills pile up, they may be taken in by offers of quick cash.
◊
By late last week, with my French consultant on a train to Alsace for a wedding, I decided to seek assistance elsewhere. My first port of call was the technical support team at GoDaddy, the Internet company that hosts my web site. I explained the problem, but was told that while GoDaddy maintained security on its side, it was not responsible for security on the user side – i.e. people with the web sites it hosts.
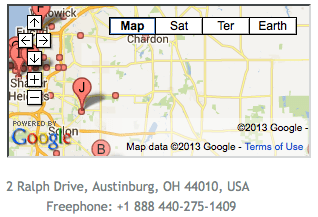
Not to be stymied, I decided to try to find out more about the hackers. I went back to the ‘INSTANT payday loans online’ site and clicked on their Contacts page. What came up was an address in Austinburg, Ohio, and a phone number.
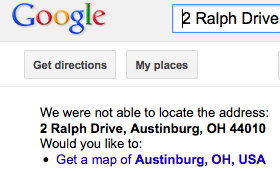
I dialed the number but a recorded message said that the phone had been disconnected. Then I tried to locate the address via Google Maps. It did not appear to exist.
At this point, getting angrier by the minute about having become the target of hackers, I decided to get in touch with the Better Business Bureau for the Austinburg district. It turned out to be in Cleveland. I was put in touch with Lou Tekavcic, a trade specialist at the bureau, who confirmed that the Austinburg address did not exist and very helpfully supplied me with information from WHOIS, a registry of information about web users worldwide.
WHOIS identified both payday loan sites as having been recently created – the ‘blatpaydayloans’ site on April 22 and the ‘payday2loan3’ site on May 28, just three days before it was surreptitiously inserted into my blog. (I later learned that other payday loan sites had been inserted as early as March). WHOIS also identified both sites as being registered with the same domain manager, a company called Gransy located in Pardubice, a small city in Czech Republic about 60 miles east of Prague.
This does not mean that Gransy was responsible for the hacking. The domains are registered through the Czech company, but Gransy has nothing to do with how people use the web sites registered there. Still, it was the first link in a chain.
I looked Gransy up on Google to try to get more information about the company, and discovered that it manages hundreds of thousands of Internet domains, along with a sister company called Regtons. Determined to get to the bottom of this, I went to the Contact page on the Regtons site and found a Prague phone number, which I promptly called. I wanted to know whether Gransy/Regtons was aware that domains it had registered were being used by hackers. The man who answered spoke enough English for us to understand each other. He said that all queries had to be emailed.
The last thing I wanted to do was to send a message via the Internet to a company involved, even marginally, in the hacking of my Internet site. ‘No,’ I replied, ‘I need to discuss this with a real human being.’ He gave me a five-word answer: ‘I am real human being.’ And then he hung up.
Pardubice, a pretty city on the River Elbe, has the dubious distinction of being the place where Semtex plastic explosives are made. Other than that I found little of interest about the town. And even though the hackers had registered their site with Gransy, there was no guarantee that they themselves were from Pardubice or Prague. They could have registered their sites from anywhere, really – Russia, China, wherever.
But I did discover more about Gransy, a company that has been little mentioned in the American press. Last September, a domain marketplace called Afternic, based in Waltham, Massachusetts, announced that Gransy had joined as a premium partner. (In one of the many odd footnotes to this story, Afternic chose to make its announcement on Sept. 11.)
Afternic is part of NameMedia, also based in Waltham, which bills itself as ‘the leading marketplace for premium domain names.’ The company, founded in 2005, boasts that its web sites receive more than 70 million visits a month. Its annual revenues amount to $60 million, according to the company. This is clearly big business, and Gransy is part of it.
I contacted Afternic to try to find out whether they were aware that their associate had registered domains used by cybercriminals, but a spokeswoman was not available for comment.
◊
Meanwhile, all this information wasn’t getting me very far in terms of solving the problem. My blog was still hacked, as readers confirmed each time they received a new email update. In fact, a new problem arose: when readers tried to use the print icon to print my recipes, they informed me, they got a text at the top of the recipe saying: ‘Apply here cash advance 100% secure’, with ‘cash advance’ being an active link.
 Clearly I needed to find someone with the expertise to get into my site and expel the intruders. I did a little searching on the Internet. This led me to Michael VanDeMar, a web developer in Largo, Florida, who specializes in dehacking web sites.
Clearly I needed to find someone with the expertise to get into my site and expel the intruders. I did a little searching on the Internet. This led me to Michael VanDeMar, a web developer in Largo, Florida, who specializes in dehacking web sites.
To make a long story short, Michael VanDeMar solved the problem. To the best of our knowledge, the hackers are no longer present on my site. But where this gets really interesting is in the details.
I knew nothing about how hackers operated before last week when I learned of the bad link in my email update. Now I know that this sort of link is called ‘malware’ and that it can be inserted into the pages of an unsuspecting blogger via a ‘back door,’ through a technique known as ‘cloak hacking.’
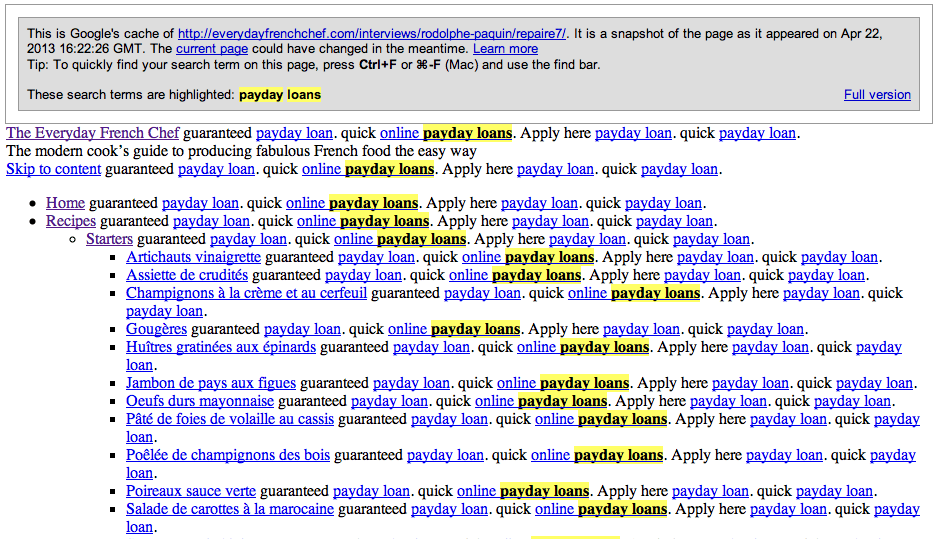
Michael VanDeMar sent me a snapshot from Google’s cache of one of my blog pages as it appeared on April 22. He had done a search for ‘payday loans.’ Amid links to recipes for French starters like artichokes with vinaigrette sauce and chicken liver pâté, the hackers had embedded links to one of their loan sites. This is how it looked:
In the insidious, malevolent and lucrative business of cybercrime, the scheme does have a certain brilliance. The links to the hackers’ loan site are present on every blog page, but they are invisible to normal visitors. As Michael VanDeMar put it, the spam is ‘cloaked.’
Although the site may appear to be fine, he said, ‘if a search engine such as Google or Bing visited your site, the spam was shown to them.’ The simple fact that the link has been spotted drives the intruders’ site up in Google’s rankings, allowing it to appear high in the list when somebody searches for online loans. In other words, it allows the cybercriminals to attract business, and also to obtain personal data from the loan applicants.
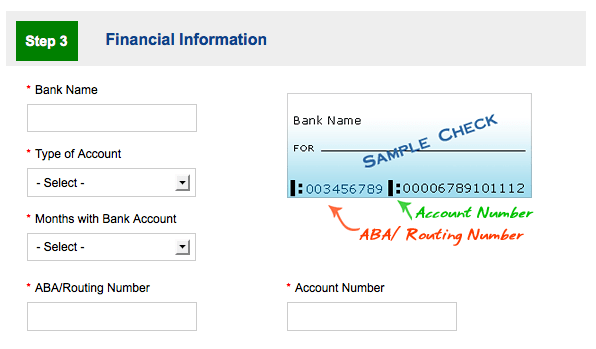
I clicked on the Apply page of payday2loans3.com to see what kind of information a loan applicant is asked to provide. The list includes: name, address, date of birth, Social Security number, driver’s license number, name of employer, monthly income, next scheduled pay dates, bank name and account number, and the bank’s routing number. It is all too easy to see how such data could be maliciously used by a cybercriminal interested in identity theft.
But Michael VanDeMar cautioned that my hackers were not necessarily making money through identity theft.
‘It is possible that they were attempting to steal info, but it is also just as likely that they were attempting to generate money via lead generation on legitimate sites,’ he said.
‘What they would do is sign up as affiliate marketers, and get paid for generating leads to legitimate sites, or redirect the traffic to some other website that is monetized in some way, such as with AdSense or another ad network.
‘In some cases they will also deliver a PC virus payload, which would then attempt to infect the visitor’s computer. That in turn would allow them to add the infected computer into a bot network, which can be used for further hacking, sending spam, DDoS [distributed denial-of-service] attacks on servers, etc.’
◊
I wasn’t sure I fully understood this explanation, for the workings of the cybercriminal mind are a bit beyond my grasp. But I had another question. If the domain registrar wasn’t responsible for hosting the hackers who attacked my blog, who was?
‘In fact, the sites are hosting on web hosts all over the world,’ Michael VanDeMar said. ‘cash2advance3.com is hosted at abuzam.net, which is a Russian web host that allows hackers. blatpaydayloans.com resolves to a host named serverel.net, which has a U.S. owner (probably faked) and appears to have an Amsterdam ip address. Three other domains that were injected – plancashadvance.com, sagacashadvance.com and krotpaydayloans.com – are all being hosted in Scranton, Pennsylvania, by a legitimate hosting company named Network Operations Center Inc.’
But how did the intruders get into my site in the first place? After ruling out various other methods, Michael VanDeMar concluded that my blog had been hacked in a way that occurs when ‘there is an insecurity at the hosting level that allows one infected site on the server to infect other sites on the server.’
In other words, I needed to go back to my host – GoDaddy – to see whether my site had been infected through one of its many servers.
I phoned GoDaddy’s technical support team again but was informed politely but firmly that GoDaddy couldn’t help me get rid of the intruders who attacked my blog.
‘The support for your problem is not part of shared hosting,’ the GoDaddy staffer said. ‘We don’t assist you with hackers.’
 On its web site, GoDaddy bills itself as ‘the world’s #1 domain registrar.’ I’ve been a satisfied customer for about a year and a half, ever since I set up my first web site, megbortin.com (which also turned out to be infected). I pay GoDaddy a yearly fee to retain my two domain names and to host my web sites, which I set up through WordPress, a free self-hosted blogging tool that is used by millions of bloggers around the world.
On its web site, GoDaddy bills itself as ‘the world’s #1 domain registrar.’ I’ve been a satisfied customer for about a year and a half, ever since I set up my first web site, megbortin.com (which also turned out to be infected). I pay GoDaddy a yearly fee to retain my two domain names and to host my web sites, which I set up through WordPress, a free self-hosted blogging tool that is used by millions of bloggers around the world.
When I told the support staffer that we suspected that the attack on my blog could be linked to one of GoDaddy’s servers, he replied that the company had ‘hundreds, maybe thousands, of servers’ and that hacking was ‘not something that is considered to be a basic problem on our servers right now.’
The support staffer said that the hackers may have penetrated my web site due to a security problem with my WordPress account.
Before ending the conversation, I asked the support staffer what would happen if the problem recurred. Could GoDaddy protect me from future attacks, or could my site get hacked again? His reply was hardly reassuring.
‘If the CIA’s web site can get hacked,’ he said, ‘anybody’s web site can get hacked.’
◊
Following this conversation, I contacted GoDaddy’s corporate headquarters in Scottsdale, Arizona, to ask for an official comment on the company’s policy on hacking. They got back to me yesterday, and last night I spoke by phone with Todd Redfoot, GoDaddy’s chief information security officer.
He apologized for what had happened, saying that the support staffer ‘should have escalated your problem to an advanced technical support team. With your permission, that support team would go onto your server and look for anything malicious.’
And what was GoDaddy’s policy on hacking?
‘If it’s a server issue, then we’ll address the server issue,’ Todd Redfoot said. ‘If it’s a content issue, we would assist the customer in fixing the issue themselves and securing the account.’
He then offered to look into the specifics of the attack on The Everyday French Chef. This morning I received his preliminary report:
‘Our logs show that your account (everydayfrenchchef.com) was actually altered on March 6. An attacker, coming from Canada, logged into your WordPress admin page at 0835 AM (GMT) with valid credentials. They then used the theme-editor to modify your 404.php file to allow them to upload additional files. These additional files allowed them to come back later, without a log in (in case you noticed and changed your password), to make additional changes to your website. These files are called ‘Backdoor Shells’, and are used to maintain control of websites after the initial compromise: http://en.wikipedia.org/wiki/Backdoor_Shell.
‘Then, on March 27, at 0635 AM (GMT), the attacker came back, this time from a Germany computer. The attacker then added the ‘Pay Day Loans’ text to various pages – the text that you ultimately discovered. They did this by posting a command to the files (backdoor shells) that they uploaded earlier in the month.’
This intriguing explanation indicates that an international gang of hackers got into my site by somehow obtaining my WordPress password. How they may have done that is still not clear to me.
◊
Michael VanDeMar, who has spent years studying hacking issues, suggested that firms like GoDaddy might have business reasons for preferring to hand off responsibility for problems like the one I experienced. (He made this comment after I unsuccessfully tried to get help from GoDaddy’s support team, and before I received Todd Redfoot’s report.)
‘If they admit that there’s a problem on their server, that could open a class-action lawsuit,’ he said. ‘It’s a financial issue.’
While trying to fix my problem, he tracked down the address of my GoDaddy server. Using the Bing search engine, he found that numerous other sites on the same server had been affected by payday loan hackers, among them the sites of a Cape Cod poultry farm, an artist in Portland, Oregon, and a real estate broker in Montreal.
So this is where we stand. Bloggers as unlikely as artists, farmers and writers have become the victims of cybercriminals who are promoting loan schemes in a fraudulent way.
Is there any way to pursue these Internet fraudsters? This is a question I put to Lou Tekavcic of the Cleveland Better Business Bureau.
‘It’s an uphill battle,’ he said. ‘These sites collect confidential information from consumers who unwittingly expose themselves to identity theft and, regrettably, law enforcement faces an ongoing battle trying to shut them down.’
 Lou Tekavcic provided me with links to IC3, a partnership between the FBI and the National White Collar Crime Center that aims to combat Internet crime. I took a look at these links, which confirmed that Internet fraud is a major, and growing, phenomenon.
Lou Tekavcic provided me with links to IC3, a partnership between the FBI and the National White Collar Crime Center that aims to combat Internet crime. I took a look at these links, which confirmed that Internet fraud is a major, and growing, phenomenon.
In its latest annual report, released in mid-May, IC3 says it received more than 280,000 reports of online criminal activity in 2012. Total reported losses via cybercrime amounted to more than $525 million, an increase of 8 percent over the previous year. And that’s just the reported losses.
Even though I have not suffered financial consequences from the hacking of my blog beyond the fee I paid Michael VanDeMar, I plan to file a complaint with IC3. To put it plainly, I am incensed at the idea that criminals are using my creative work to defraud other people.
I would love my complaint to lead to a worldwide Interpol search to hunt down these cybercriminals. But I doubt that will happen anytime soon. And I fully expect my blog to be hacked again – if not this year, then sooner or later.
That won’t stop me from sending my recipes into cyberspace. I love French cuisine, enjoy writing about it, and won’t be deterred by a band of Internet thieves.
Besides, if it happens again, I know there’s someone looking out for me in California. That person, as he put it himself when he first mentioned the problem, ‘being your brother who’s got your back and everything.’
◊
 If you found this article interesting, please share it with others who may have experienced similar problems, or who may want to know more about Internet hacking. There is a space for comments below.
If you found this article interesting, please share it with others who may have experienced similar problems, or who may want to know more about Internet hacking. There is a space for comments below.
— Meg Bortin








Meg, Thank you for writing this. I have just hired Michael to help with my site. It wasn’t payday loans… but other malicious content. =(
I am so glad that I found you and something possibly joyous may derive from this awful event. I was in Paris last year and I had the most amazing duck confit. Do you happen to have a recipe for that? I doubt I could come close to replicating the delicious dish but I’m willing to try.
Thanks so much!!!
Dear K, I’m so glad this post proved useful, and I highly recommend Michael VanDeMar, who has helped me resolve website problems on several occasions. Regarding the duck confit, yes, there is a recipe on the site. Here’s a link to the blog post (from December 2014), which you may find interesting, and you can get from there to the recipe. If there are other French dishes you’d like to create, you can easily find them via the Search area on the home page. Good luck with your internet issue, and all best from Paris. Meg
Probably the most useful article I have seen about the payday-loan scammers’ hacking of GoDaddy-hosted WordPress sites. Thank you. I agree that the way forward is, in the US, to press for investigation by agencies such as the FBI, and in Britain, the police, who claim to be upgrading their internet-crime squad. You were able to make progress in a short time. The authorities’ resources are far greater than one person’s. What’s stopping them?
Incidentally, your site is great. I am sure you have, uhm, cooked up some interest among publishers.
Many thanks, David. The article was relatively easy to research. I did it in a couple of days. Of course, it helped that I was very angry about being hacked, and had a lot of energy to try to track down the hackers. I didn’t get to the end of the trail by any means. That is up to the relevant authorities. Like you, I’d like to ask: What’s stopping them?
This is fascinating – in a scary way. Thanks for writing this post. I hope I will never have to refer to it but should I need to, it’s extremely comprehensive – great info here.
The globe trotting criminals may not be so globe trotting. There are IP-masking services that allow users to appear to be anywhere in the world. The cyber criminals could have been in one location the whole time.
Interesting. Please tell us how that works.
I admire your sleuthing.
Scary how vulnerable we all are.
Glad your brother watches your back.
Great work, Meg! Your tenacity amazes me. I would have thrown in the towel long before.